More attacks on Google Workspace and Office365
On Nimblr, we are receiving more and more reports of businesses being affected by scams where payment details sent by email from trusted senders have been modified. The approach is not new, but it remains an effective method of obtaining both money and goods. Most of the attacks occur in the Office365 environment, but similar attacks have also been noted in Google Workspace.
How it works
The attack starts with the attacker gaining access to a user's email account, often through a fake login page where the user enters their password in good faith. The attacker uses the password to log into the victim's webmail. There, the attacker creates email rules that forward or copy the email communication to an external email address.
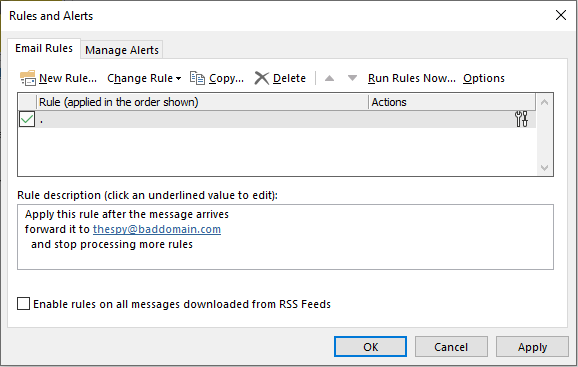
In some cases, the rules are based on specific criteria, such as only forwarding emails containing the word "invoice" or "payment". In some of the attacks reported by Nimblr, the email does not reach the intended recipient until after the attacker has had the opportunity to modify the content.
Once the insidious email rule is in place, the attacker simply waits for the right moment. By invisibly examining the victim's communication, the attack can go on for a long time, and so when, for example, a delivery address or payment information is communicated, the attacker strikes and modifies a few small details about bank account numbers or the like. Often the attack is not detected until the supplier asks where the payment for a particular order has gone, or the customer asks where his goods are.
A script that lists users with forwarding enabled
As an administrator, you may want to investigate what rules are configured in users' email clients. The easiest way is to run a powershell script in Exchange server or Office 365 instance. The script below lists all users who have forwarding enabled:
$Mailboxes = Get-Mailbox -ResultSize Unlimited
ForEach ($Mailbox in $Mailboxes)
{
$MailboxWithRule = Get-InboxRule -Mailbox $Mailbox.Alias |
where {
($_.RedirectTo -ne $null) -or ($_.ForwardTo -ne $null) -or ($_.ForwardAsAttachmentTo -ne $null)
}
if ($MailboxWithRule -ne $Null)
{
Write-Host "User $($Mailbox.PrimarySmtpAddress) has the rules:" $MailboxWithRule |
fl Name, Identity, RedirectTo, ForwardTo, ForwardAsAttachmentTo
}
}
As an end user, you can keep an eye on what rules are available via Outlook Web Access under Settings > View all Outlook settings > Rules or in the email client by clicking, in Outlook, onFile and select Manage Rules & Alerts to view active rules.

