Realistic, customer-specific simulations
Nimblr runs simulated phishing emails and smishing (SMS) attacks that mirror real attacker tactics. Simulations use realistic sender profiles, local context, and up-to-date threat intelligence so your team sees the scams they’re actually likely to get.
To make the simulations more realistic, they are customized using customer-specific data entered by the administrator, such as the name of the CFO, the customer's own logo or information about the software used in the business.
The simulated attacks are selected based on the user's history. For example, users with a history of difficulty identifying fake senders receive more simulations of this type. While other users, such as those who find it difficult to resist clicking gift card and reward offers, receive more simulations in this category.
Nimblr Instant Learning
Each simulated attack is linked to a customized reminder for those users who are tricked into clicking the link, or opening the attachment, in a simulated attack. The reminder is called Nimblr Instant Learning and displays the message that tricked the user, along with interactive tips on what to do differently next time. Along with the specific tips, the user is also offered to start an optional basic training module tied to the current simulation.
Monitoring current phishing and smishing trends
The simulated attacks are generated and sent automatically to all active users in the Nimblr security awareness program.
Nimblr monitors current phishing and smishing trends and ongoing attacks to quickly create new simulations and train users before they are exposed to the real attacks.
What's in it for you?

Micro training

Simulated attacks

Instant learning

Zero-Day Classes
%20(1).png?width=865&height=1263&name=Samishing---9-September-2025-13.59%20(1)%20(1).png)
Smishing simulation add-on

Automated reporting
Examples of simulated attacks
The simulated attacks are an important part of Nimblr Security Awareness and consist of both customised and generic simulations of phishing, fraud, malware and many other types of IT-related threats.
Microsoft Office 365
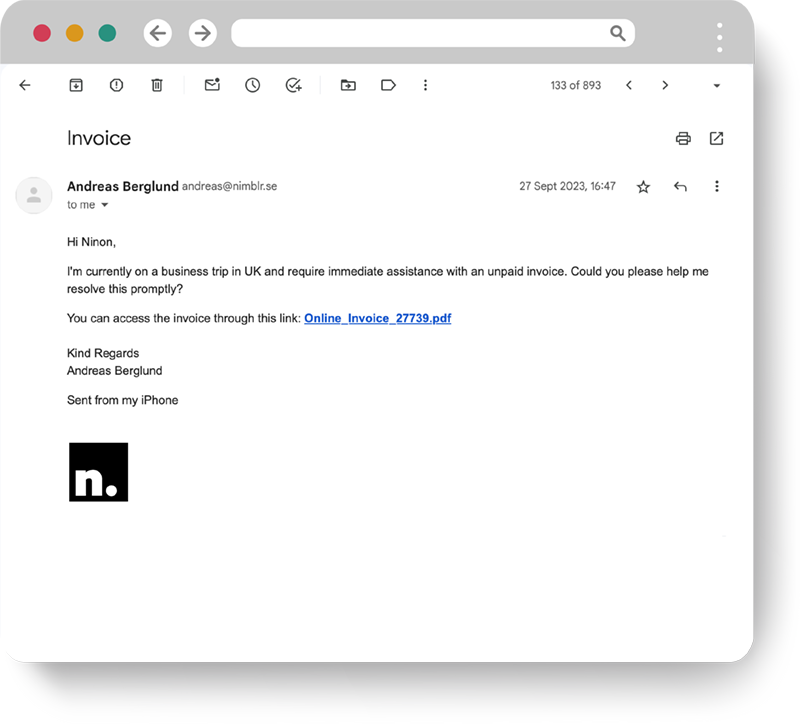
Simulated phishing that claims that the user needs to sign in to Microsoft Office 365 and verify their inbox. In real life, attacks of this type are used to get hold of the user’s log-in details.
To optimise learning, many training sessions are linked to everyday activities and are often initiated through a simulated attack. With Nimblr Instant Learning, users who are fooled by a simulated attack receive immediate feedback and concrete tips on how to avoid similar attacks in the future.

From the user’s own organisation
Simulated attack pretending to come from someone in your organisation. The data is taken from the organisation's Nimblr configuration. In reality, this type of attack has been used to infect organisations with ransomware.
Smishing simulation add-on
A simulated phishing SMS that mimics real-world tactics deployed by scammers. This helps build security awareness and demonstrates the importance of taking care when interacting with text messages.
.jpeg?width=1179&height=2556&name=Image%20(1).jpeg)
Get a personalized demo session at your convenience.
Book a demo meeting and let one of our experts walk you through Nimblr solution, the platform, and how quickly you can get started.

