Phishing campaign by Sweden's largest web host
A new phishing campaign is currently underway, targeting domain holders and customers of Sweden's largest web host Loopia. By retrieving information from public DNS servers, the attackers can identify email addresses linked to selected web hosts and domain name registrars.
The attackers claim that a session to the Loopia customer portal has not been terminated correctly and the recipient is asked to log in and terminate the session correctly. The purpose is to obtain the login credentials to Loopia's customer portal and thereby gain the ability to e.g. redirect email traffic so that it can be easily intercepted, spread malicious or redirect web traffic to another site.

If you follow the link in the email, you end up on a website similar to Loopia's own. The connection is over https with a valid certificate. But pay attention to the URL - it does not match Loopia's web address at all.
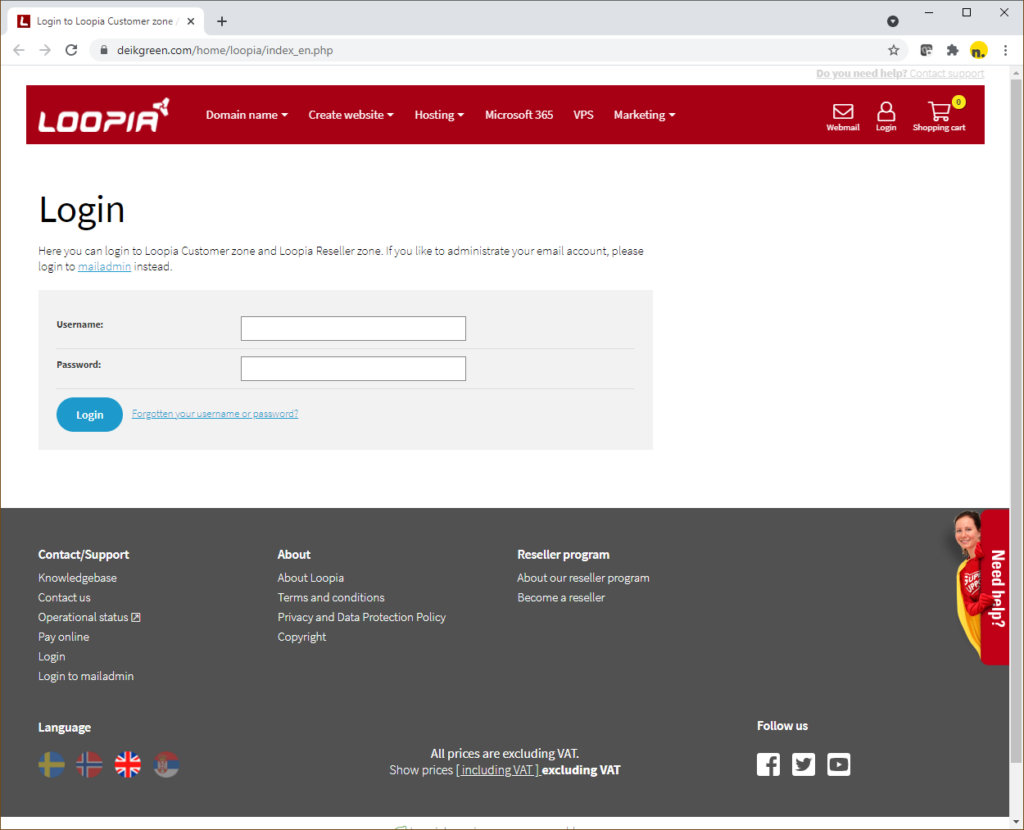
The fake website is located on a US server and hides in a subdirectory of an online shop. Nimblr has notified the website owner of the problem.
This is not the first time that attackers have targeted Loopia's customers; similar practices have been going on for some time in various forms. Nimblr has previously recorded phishing messages claiming that email addresses need to be verified or that the fee for a domain name has not been paid.
